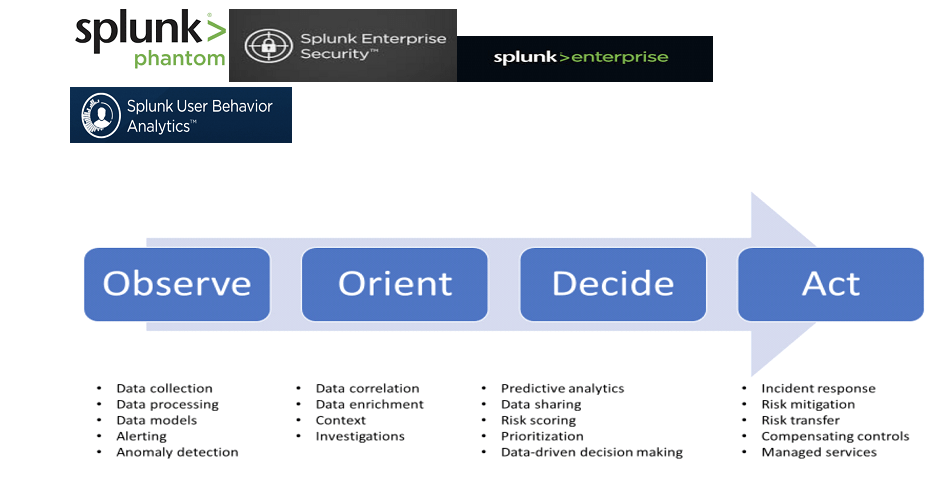
At the end of 2020, as some of you might remember, there was a massive vulnerability that became known as the Solar Winds vulnerability. And in the wake of the SolarWinds vulnerability, I thought it would be helpful to put something together to talk about how critical mapping out your security monitoring coverage truly is.Continue reading “Scaling Security Monitoring with MITRE ATT&CK”
Author Archives: bcyates
Tuning Your Search Head When Reach Concurrency Limitations
When you see the error for reaching max historical concurrent level jobs, or you get frequent messages like “waiting for queued job to start”, you are hitting either the User-level concurrent jobs limitation, the role level concurrent jobs limitation, or the system level concurrent jobs limitation. We will talk through each of these, where toContinue reading “Tuning Your Search Head When Reach Concurrency Limitations”
Splunk.Myths.Misconceptions
Before I moved over to the PS world, I was a Splunk admin who thought he had it all figured out. I had been working with Splunk for almost three years before I made the jump and got hit with the realization that I didn’t know near as much as I thought I did. IContinue reading “Splunk.Myths.Misconceptions”
Use Case Template
Use Case Template Each section of the use case template is below in a heading style with the instructions on populating that section between square brackets. General advice on implementing the use case is given in angle brackets. After this, build a document with these headings, populate it with information relevant to your organization, yourContinue reading “Use Case Template”
ES Implementation Checklist
Introduction Almost every customer that purchases Splunk’s Enterprise Security will also use Professional Services to implement the product. This guide will serve as a checklist to help you ensure you are prepared for the most successful Enterprise Security deployment as possible. We will identify the Who, What, Why, and How of a successful ES deployment.Continue reading “ES Implementation Checklist”
Dos and Donts of Splunking Your Syslog
Syslog is plentiful in all environments, no matter what the size may be and Splunking your syslog is something that inevitably happens, one way or another. And believe it or not, there are tons of ways you can Splunk that data. As a Splunk Professional Services Consultant, I’ve seen many ways that customers send thatContinue reading “Dos and Donts of Splunking Your Syslog”
Introduce Yourself (Example Post)
This is an example post, originally published as part of Blogging University. Enroll in one of our ten programs, and start your blog right. You’re going to publish a post today. Don’t worry about how your blog looks. Don’t worry if you haven’t given it a name yet, or you’re feeling overwhelmed. Just click theContinue reading “Introduce Yourself (Example Post)”
Introduce Yourself (Example Post)
This is an example post, originally published as part of Blogging University. Enroll in one of our ten programs, and start your blog right. You’re going to publish a post today. Don’t worry about how your blog looks. Don’t worry if you haven’t given it a name yet, or you’re feeling overwhelmed. Just click theContinue reading “Introduce Yourself (Example Post)”
Introduce Yourself (Example Post)
This is an example post, originally published as part of Blogging University. Enroll in one of our ten programs, and start your blog right. You’re going to publish a post today. Don’t worry about how your blog looks. Don’t worry if you haven’t given it a name yet, or you’re feeling overwhelmed. Just click theContinue reading “Introduce Yourself (Example Post)”